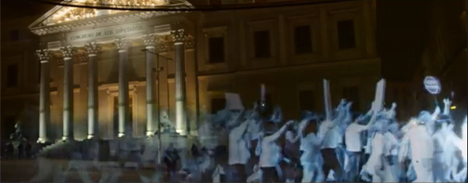From July this year, protesting in the public sphere in Spain became an expensive affair – the Citizen Safety Law, dubbed the “gag law”, criminalizes protests that “interfere with public infrastructure”. Under the new law, which was passed by the governing “Popular Party” last December, protestors are liable to be fined anything up to several hundred thousand euros for marching in front of congress, blocking a road or occupying a square. The law is the most recent in a series of attempts by the government to curb a wave of popular protests that has swept the country since 2011. With unemployment rates reaching over 25 per cent and one out of two Spaniards under the age of 25 jobless, hundreds of thousands of outraged citizens have taken to the streets, occupying squares and universities. Faced with a discredited political class, tarnished by years of political scandals and corruption, the Indignados (Spanish for “The outraged”) sought to revert to the most basic tenets of political agency by reclaiming the public sphere.
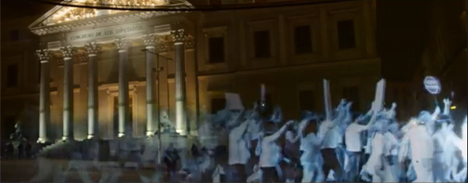
Hologram protest in front of the Congress of Deputies, Madrid, 10 April 2015. Photo: Nosomos Delito. Source:YouTube
When the movement first began, comparable protests using occupation strategies were taking place across the globe, in Tunisia, Egypt, Greece, Israel and the United States. Though many commentators pointed to the role played by new technologies such as social networks and smartphones in facilitating these protests, it was the city square, as old as political thought itself, which was the star of the show. Thus, when the ironically titled Popular Party passed its new draconic law, protesters were quick to seek an alternative solution to being physically present.
The result was a hologram protest – the first ever, as media outlets were quick to point out – skillfully choreographed and hastily projected in front of the congress gates. Specters were – for once quite literally – haunting the sterile streets, voicing the grievances of those citizens prevented from being there. The event had been rehearsed and performed in a nearby city, and the equipment (voluntarily) installed by a PR company in a clandestine operation. This was a proxy protest fit for the age of proxy politics.
The proxy, a decoy or surrogate, is today often used to designate a computer server acting as an intermediary for requests from clients. Originating in the Latin procurator, an agent representing others in a court of law, proxies are now emblematic of a post-representational, or post-democratic, political age, one increasingly populated by bot militias, puppet states, ghostwriters and communication relays.
On a broader level, proxy politics can be seen as both a symptom of crisis in current representational political structures, as well as a counter-strategy that aims to critically engage and challenge existing mechanisms of security and control.
In his book Post Democracy Colin Crouch describes the current political condition as one that increasingly relinquishes power to business lobbies and non-governmental organizations, resulting in there being “little hope for an agenda of strong egalitarian policies for the redistribution of power and wealth, or for the restraint of powerful interests”. The vision of an autonomous, potent, political subject has been devastated by the growing power of privileged elites standing at the nexus of transnational co-operations, extra juridical zones, infrastructural authorities and non-governmental organizations. To give but one example: when the house of representatives recently voted to end bulk surveillance by the NSA, it was made clear that though it would take “the government out of the collection business, it would not deny its access to the information. It would be in the hands of the private sector – almost certainly telecommunications companies like AT&T, Verizon and Sprint”. In other words, even after a seemingly successful move towards reform, it was revealed that the corridors of power lay elsewhere, between politics and the private sector. One might also think of the strong relations that Google Inc. maintains with the White House.
Which forms of resistance and evasion could apply to this vague techno-political condition? How might one avoid becoming a walking sensor platform generating indices of data?
Just as proxy politics is a condition – the name of a political regime, which thrives on obscurity, opaqueness and decoys – it may also designate the possibility of a corresponding counter-insurgency. Ideally, proxy politics encompasses a myriad of modes of withdrawal and retreat, technical as well as metaphorical – its utensils could be a VPN, a 3D scan of a fingerprint, P2P technology, a surrogate, a stock image – its outcome is always concealment, evasion, subterfuge. Hito Steyerl recently framed proxy politics as an answer to the “terror of total Dasein”. Certainly, strategies like these might be significant for an interim phase, a time during which any difference between real virtuality and virtual reality, the tangible and the digital, is increasingly difficult to discern, while it is becoming evident how severely controlled both spheres actually are.
As Alexander Galloway has observed, “instead of a politicization of time or space we are witnessing a rise in the politicization of absence- and presence-oriented themes such as invisibility, opacity and anonymity, or the relationship between identification and legibility, or the tactics of nonexistence and disappearance, new struggles around prevention, the therapeutics of the body, piracy and contagion, informatic capture and the making-present of data (via data mining)”.
Once considered to be a deterritorialized technology, the Internet is being reterritorialized by way of security mechanisms, the TCP/IP control protocol and national jurisdiction. Emblematically, the NSA have attempted to map the Internet using a program called Treasure Map.
The shadow-like figures in the hologram protest embody a double movement – a process of deterritorialization and reterritorialization. First, slogans and shouts were crowd-sourced online, then synced with holographic images filmed in a nearby city, where the distances and angles of the scene in front of congress were meticulously reproduced.
Finally, scattered, dispersed voices were composited, montaged and reassembled in public space. The blue-ish tone of the hologram projection is reminiscent of surveillance camera footage, alluding to the popular depiction of a dystopian totalitarian state. Instead of public space, the simulated protesters inhabit a new medium, the proxy. In this case, a hologram, a digital object which manifests itself in three-dimensional space. Could these people be convicted on the basis of the actions of their holographic avatar? Would face recognition software criminalize them, or their doubles? Here, the individual is rendered an intersection of profiles and data. As Nishant Shah has recently put it, the “regulation of data is closely tied in with regulation of bodies, and […] a failure to effectively govern data puts biological bodies in conditions of precariousness and danger.”
While constellations of physical and digital spaces are under continuous negotiation, recent publications have shifted focus, either towards the physical infrastructures (Keller Easterling) on which global networks rely, or towards an expanded definition of networks as “imagined networks” (Wendy Chun) that takes into consideration “gaps between the experience and the representation of networks”. According to Chun, networks enable us to imagine the unimaginable, like global climate change or global capital, as they create unforeseeable futures. Within these imagined networks, we are a series of “you’s” rather than a collective “we”. This non-communitarian tendency might be considered as one of the shortcomings of proxy politics and its apparatus. The body double, the scan or VPN all refer to the individual user, rather than to a collective. But might the proxies mobilize en masse?
When the Turkish government banned Twitter during March last year, protesters and users turned to Google’s public DNS, using it to circumvent the ban, while spreading the word both in real life meat-space via graffiti, and online virally. As with the hologram protest, once again, public space and the screen were for a moment conflated. The proxy, whether as hologram or communication relay, metaphor or infrastructural intervention, brings forth the possibility of political agency in an age in which ruling powers increasingly enjoy a prerogative to obscurity, while political subjects are rendered increasingly transparent. Proxy politics hinges upon a struggle for opacity, it is both a new form of power as well as a mode of resistance.